The Ultimate Guide to IoT Security Challenges and Solutions
Author: Laila Meraj
7 Feb, 2025
The Internet of Things (IoT) has transformed how we interact with technology. Understanding the intricate landscape of IoT security is not just important, it’s imperative. IoT devices have become increasingly sophisticated but so have the threats that target these interconnected systems. So, let’s discuss these challenges and solutions right here in this blog.
Xorbix Technologies addresses these complex challenges, offering comprehensive Internet of Things development Services that prioritize security and innovation.
The Threats of IoT
Unauthorized Access and Device Vulnerability
Modern IoT systems are intricate networks of interconnected devices, each representing a potential entry point for cybercriminals. From smart home devices to industrial sensors, these technologies are increasingly becoming targets for sophisticated cyber-attacks. The primary challenge lies in the diversity and complexity of these devices, which often have varying levels of built-in security measures.
Xorbix recognizes that device vulnerability is not just a technical issue but a strategic concern. Our approach focuses on creating strong security frameworks that anticipate and mitigate potential breaches before they occur.
Data Privacy and Encryption Challenges
The exponential growth of IoT devices generates massive amounts of data, personal, corporate, and sensitive information that becomes a valuable target for malicious actors. Traditional encryption methods are often insufficient in protecting this complex data ecosystem.
Our Internet of Things solutions implement advanced encryption protocols that go beyond standard practices. By developing multi-layered security architectures, we ensure that data remains protected throughout its lifecycle, from collection to transmission and storage.
Critical Security Risks in IoT Environments
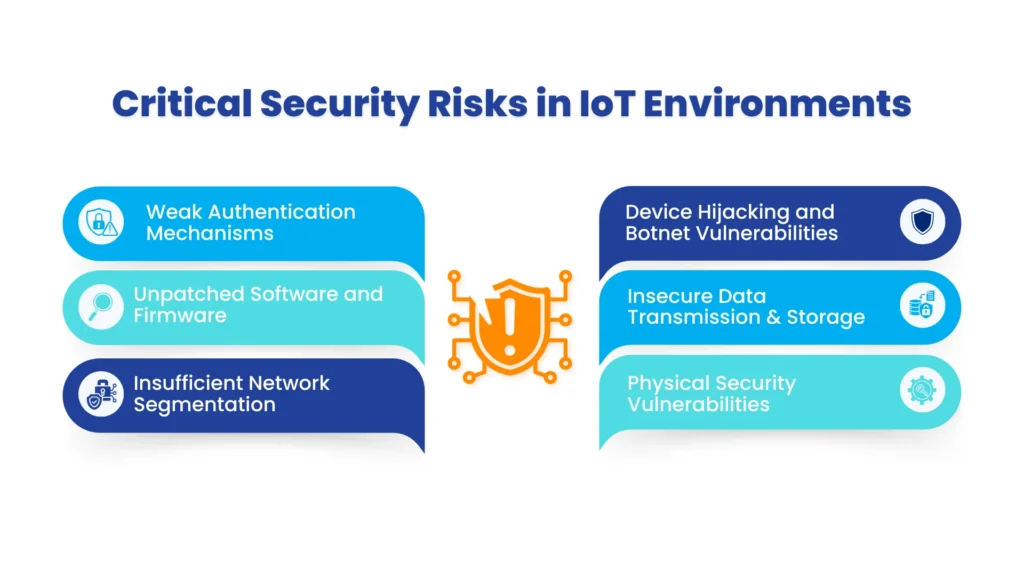
1. Weak Authentication Mechanisms
Many IoT devices continue to rely on default or easily guessable credentials, creating significant security vulnerabilities. Attackers can exploit these weak points to gain unauthorized access, potentially compromising entire network infrastructures.
We address this challenge through:
- Advanced multi-factor authentication
- Biometric verification processes
- Dynamic credential management systems
2. Unpatched Software and Firmware
Outdated software represents one of the most significant security risks in IoT ecosystems. Manufacturers often struggle to provide timely security updates, leaving devices exposed to known vulnerabilities.
Our development services include:
- Automated patch management
- Continuous vulnerability assessment
- Proactive firmware update strategies
3. Insufficient Network Segmentation
When IoT devices share network resources without proper segmentation, a single compromised device can potentially expose an entire infrastructure to risk. This interconnectedness demands sophisticated network design and monitoring.
We implement intelligent network zoning, granular access control mechanisms, and real-time threat detection systems to ensure the risk is addressed properly.
4. Device Hijacking and Botnet Vulnerabilities
Unsecured IoT devices can be easily compromised and recruited into massive botnets. These networks of infected devices can be used for distributed denial-of-service (DDoS) attacks, cryptocurrency mining, or large-scale data theft. Attackers can take control of devices with minimal effort, using them as entry points into broader network infrastructures.
Mitigation strategies include:
- Implementing strong device authentication
- Regular security firmware updates
- Network traffic monitoring and anomaly detection
5. Insecure Data Transmission and Storage
Many IoT devices transmit sensitive data without adequate encryption, leaving information vulnerable to interception. Weak communication protocols and inadequate data protection mechanisms can expose personal, financial, and operational data to potential breaches.
Key protection approaches:
- End-to-end encryption
- Secure communication protocols
- Data anonymization techniques
6. Physical Security Vulnerabilities
IoT devices are often deployed in physically accessible locations, making them susceptible to direct tampering. Unauthorized physical access can compromise device integrity, allowing attackers to extract sensitive information or manipulate device functionality.
Defense mechanisms include:
- Tamper-resistant hardware design
- Physical access controls
- Intrusion detection systems
- Encryption of device storage and configuration
Emerging Solutions in IoT Security
AI-Driven Security Solutions
Artificial Intelligence is revolutionizing IoT security by enabling predictive threat detection and autonomous response mechanisms. Machine learning algorithms can analyze network behavior, identifying anomalies and potential security breaches in real-time.
Our research and development team leverages AI solutions to create adaptive security frameworks that evolve alongside emerging threats. By analyzing patterns and predicting potential vulnerabilities, we stay several steps ahead of cybercriminals.
Blockchain for Enhanced Security
Blockchain technology offers promising solutions for securing IoT ecosystems. Its decentralized and immutable nature provides an additional layer of security that traditional methods cannot match. Our team of experts explore this integration to ensure data integrity, create transparent transaction logs, and develop tamper-proof authentication mechanisms.
Practical Mitigation Strategies
1. Comprehensive Security Audits
Regular, thorough security assessments are crucial in maintaining a strong IoT infrastructure. These audits help identify potential weaknesses, validate existing security measures, and recommend improvements.
Our approach includes penetration testing, vulnerability scanning, and compliance verification to enhance the security of IoT systems.
2. Employee Training and Awareness
Technology alone cannot guarantee complete security. Human factors play a critical role in maintaining secure IoT environments. Comprehensive training programs can significantly reduce the risk of security breaches caused by human error.
We offer customized security awareness training, simulated threat scenario workshops, and continuous learning resources to help avoid human errors that can cause security risks.
The Future of IoT Security
As IoT continues to expand, security will become increasingly complex and critical. Emerging technologies like 5G, edge computing, and quantum encryption will introduce both challenges and opportunities.
Xorbix remains committed to staying at the top of these technological advancements, continuously innovating our IoT services to provide unparalleled security solutions.
Conclusion
Navigating the intricate world of IoT security requires a proactive approach. By understanding potential risks and implementing strong security strategies, organizations can gain the advantages of connected technologies. A leader in technological innovation, Xorbix Technologies provides comprehensive IoT security solutions that protect, optimize, and revolutionize digital infrastructures. Our commitment to excellence drives us to develop state-of-the-art strategies that keep our clients ahead of emerging technological challenges.
Read more about our related services:
- The Role of IoT in Energy Management
- Databricks Lakehouse: The Key to Scalable Cloud Data Solutions
- The Essential Guide to Mobile Application Development for Business Growth